
As with all major sporting and entertainment events, the goal is for everyone using a ticket to have purchased it from the authorized ticketing entity and to have a seamless experience both when they pick it up and when they present it at the venue.
- By Cesare Paciello
- Jul 11, 2018

There are many aspects to consider when developing a retail security strategy, including loss prevention, physical security, asset protection, risk management, and IT.

Today’s facility operators must prepare for virtually any event from vandalism to a terrorist attack. With facilities ranging in size and use—from an emergency communications center to a multi-family apartment building—there’s no readily available one-size-fits-all security plan.
- By Dana Pruiett
- Jul 11, 2018

While the threat of terrorists planning to attack soft targets, such as stadiums, increases, stadium security professionals must look for the weak points throughout their facilities to determine where fanatics are most likely to assail.

With more than 120 permanent network cameras in place at Volunteer Stadium and Howard J. Lamade Stadium, Little League International works to add new technologies each year to keep the installation as secure as possible
- By Courtney Dillon Pedersen
- Jul 11, 2018
Red Hawk Fire & Security, LLC. has announced the purchase of Security and Data Technologies, Inc., (SDT) to continue extending its reach to customers in Philadelphia, and the tri-state area of Eastern Pennsylvania, Central and Southern New Jersey and Delaware.
I’m old enough to remember fire alarm drills and hiding under my desk as a youth. The fire alarm drills were great because we were able to leave the classroom and go outside. I never understood hiding under the desk, but went along with it anyway. That’s the world I grew up in.
- By Ralph C. Jensen
- Jul 11, 2018

Wi-Fi is a technology based on the IEEE 802.11 suite of standards that uses radio frequencies (RF) extend wired Ethernet-based local area networks (LAN) to Wi-Fi-enabled devices, allowing the devices to receive and send information from the internet.
- By Andrew Jimenez
- Jul 11, 2018

Our goal of clustering attacks on web applications is two-fold
- By Gilad Yehudai
- Jul 11, 2018

With police departments often being under budgeted and over worked, resulting in reduced patrols and delayed response, many business owners have come to expect that valuable assets stored outdoors are going to be subject to theft and vandalism, and these costs just need to be absorbed.
- By John Distelzweig
- Jul 11, 2018

As Foxwoods grew and expanded, so did the need for a state-of-theart, integrated video surveillance system to provide necessary coverage and security for the gaming facilities.
- By Michael Lohr
- Jul 11, 2018

The new and growing interest in the technology sector has given rise to a new phenomenon known as “Tech tourism,” whereby tech companies have seen ever increasing numbers of visitors being attracted to their sites as tech enthusiasts undertake a kind of digital pilgrimage.
In 2017, the HUSD sought to upgrade existing mechanical locks to electronic locks. With more than 5,000 doors across 28 campuses districtwide, the transition was sure to be a significant undertaking.
It has become crystal clear to me that integrators and distributors are experts in product development in this industry.
- By Ralph C. Jensen
- Jul 11, 2018
The modern workplace is increasingly mobile. The prevalence of secure mobile internet and emphasis on face-to-face collaboration has seen corporations increasingly emphasize remote work for their employees.
- By Annie Asrari
- Jul 11, 2018

Arkansas looks for ways to boost security on campuses.
- By Sydny Shepard
- Jul 10, 2018

Timehop disclosed a security breach that has compromised the personal data, including names and emails, of its 21 million users
- By Sydny Shepard
- Jul 10, 2018

Catholic churches in Fort Worth have removed signs banning guns, but that doesn't mean the policy has changed.
- By Sydny Shepard
- Jul 09, 2018

The National Zoo is the only Smithsonian public venue without security screening.
- By Sydny Shepard
- Jul 09, 2018
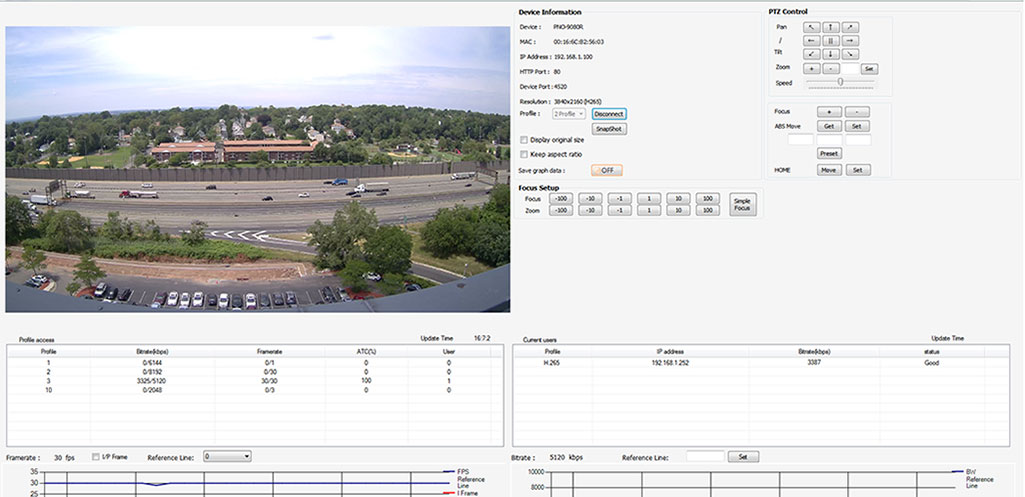
As the security industry continues to embrace 4K, Ultra HD and other high-resolution imaging formats with high bitrates, recording and storing surveillance video has become one of the main challenges facing end users and systems integrators.